2020 was anything but normal, especially for those in enterprise IT.
Though every company is facing their own unique challenges, we have noticed that certain technical use cases come up over and over again with our customers.
Since the beginning of the year, we’ve chosen the top remote work problems that enterprise IT departments are solving with Nexthink.
1. Device encryption done at scale
Many IT departments unfamiliar with remote work are struggling to quickly encrypt their devices at scale. Device encryption is the one safeguard IT can use to protect their employee devices in case of physical theft—but getting to this final stage can be challenging for tech support and disruptive for remote workers.
The problem right now is that in order to successfully encrypt a remote device, IT asks too much of their end users: employees have to initiate certain sessions and actions just to activate their encryption software, they then have to pass through multiple reboots that take time out of their workday.
Aside from the general disruption this causes, employees get no assurances either—they won’t get answers to like:
Will I be able to work once the encryption process has started?
Do I need to stay connected to my device while the encryption is in progress or can I leave?
Once my hard drive is fully encrypted, will I get a confirmation?
For IT, they have to deploy significant time and support staff to guide employees through this multi-step process—all while simultaneously performing complicated backend work, like cross-checking technical security protocols in their registry and WMI tables.
“
In just a few days, we deployed more encrypted laptops than in the last 5 years.
IT Director
National Defense Organization
Attacking this problem at both ends, Nexthink has been helping IT support to encrypt their devices at scale with the help of powerful remote actions and messages that guide employees in record time. For example, a national defense organization recently used Nexthink’s Act & Engage modules to encrypt 15,000 remote devices in just 3 days, and without a single remote worker having to ask IT for help.
2. Effective IT comms & employee feedback
IT communications and outreach has never been more important than now. Whether it’s communicating to remote workers on how to connect to their VPN, offering advice to improve a weak Wi-Fi signal, or sharing pertinent COVID-related news, IT is being asked to do it all but they don’t have the right tools to do the job.
Unfortunately, tech support relies too heavily on email and popular messaging apps to communicate with remote workers. The former (email), is notoriously ineffective for 3 reasons:
- Messages can end up in a spam folder
- Targeting by email address doesn’t always account for every employee (for example, contractors)
- Not every person actively checks their email (or has it open).
And popular messaging tools are equally as ineffective because they can succumb to certificate expirations or bugs, and not all employees may use them.
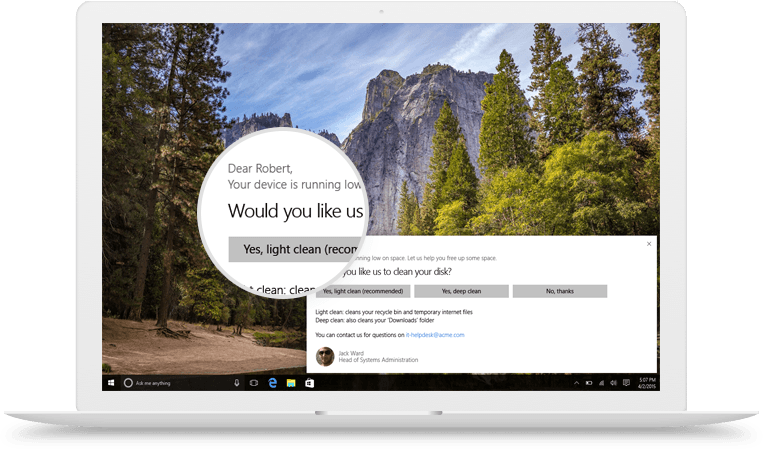
Some IT support teams are circumventing these limitations by using Nexthink’s Engage module.
They can set either one-off or perpetual campaigns to target exact user groups with helpful messages that are impossible to ignore. With 80% response rates, IT departments can collect critical insights from employees in single, multi, and opinion-based answer formats. And this sentiment data isn’t only relevant to IT, HR can also leverage this information to better understand how employees are coping with their current workload and remote setup.
3. VPN health & business continuity
Most businesses use a VPN (or multiple VPNs) as a means to sustain their company’s productivity and protect their data, devices, and remote employees.
For IT, monitoring the company’s VPN can be an enormous undertaking: they have to constantly check that tools don’t exceed the network’s limit; discern if certain power-heavy apps need to be rerouted to their proxies; identify any connectivity issues, hard resets, and a host of other variables. If IT cannot deliver the appropriate response to problems in real-time, the VPN can crash and knock any and all employees on it offline.
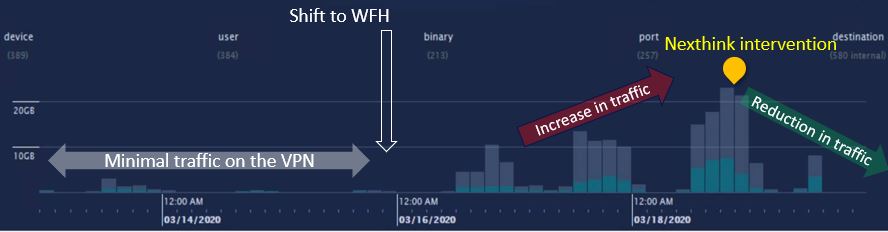
Thanks to Nexthink’s comprehensive dashboards, tech support is able to track in real-time all devices, users, binaries, ports, and destinations within their VPN setup.
Sometimes customers even use Nexthink’s insights to isolate employees that don’t need to be connected to the VPN in the first place.
For example, one customer last month experienced a spike in traffic nearly 5x their average because users assumed they needed the VPN to access every single one of their intranet applications—but a third of those workers only needed Office365, a suite of tools that could’ve been easily accessed outside the network!
4. Version control
One of the most widespread challenges IT encounters with remote work is version control.
Knowing which software applications are current and which are soon to expire can save businesses from downtime and productivity loss.
For example, if an employee uses Skype as their principal communication tool but their certificate expires, they will be thrown off the application and unable to collaborate with colleagues.
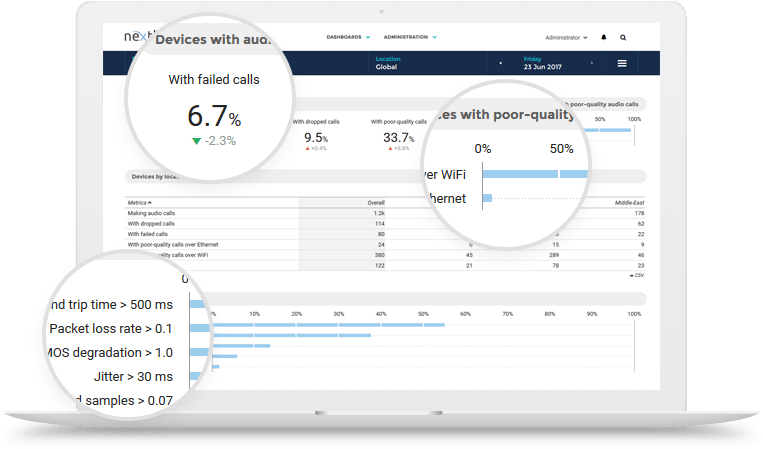
Drill-down into your collaboration tools & ensure they are always up to date.
It’s also important for IT to know which devices and business applications are set for upgrades, and which might be vulnerable to security breaches (think Windows 10, for example).
A few weeks ago, one IT department used Nexthink’s dashboards to quickly isolate employee subgroups that hadn’t updated particular business applications for things like SharePoint, Office365, and Slack. Within the same Nexthink platform, IT was able to update those users with the most recent application versions, which ensured their colleagues stayed productive and protected.
5. Offsite Multi-Factor Authentications
Many remote workers have also been forced to pass through new multi-factor authentications that have invariably tripped them up.
Multi-Factor Authentication (MFA) is a common IT process where an end user must successfully pass two or more pieces of evidence (or factors) to an authentication mechanism—like a pin number or security code sent to your cell phone or personal email address.
Normally, when a worker is onsite, they don’t have to worry about passing through an MFA because the company’s local network runs the authentication check automatically.
But for remote workers this can be different.
To circumvent this problem, IT departments are using Nexthink to send targeted campaigns that guide remote workers on their own accord. For example, a few weeks ago, employees at a large packaging company phoned into the IT help line en masse, looking for assistance with their MFA process so they could connect to the VPN. The average wait time per worker lasted over 15 minutes.
“
We're really excited about how we were able to turn around this MFA project, we've never been able to do something like this before in such a short period of time.
Head of End User Computing
Packaging Company
Within 24 hours, IT sent out a targeted Nexthink campaign that detailed how users could quickly complete the MFA process. After 3 days, over 300 remote employees successfully activated their MFA and connected to the VPN without contacting IT for help.
6. Deeper incident data to show the full story
Popular ITSM tools like Splunk, ServiceNow, and even data mining software like Power BI, are very useful for IT from a systems-centric standpoint.
However, tools like those only reveal half the story. None of them can show IT support the real-time information from their employees’ digital experiences nor the critical performance data going on in their devices and applications.
Yet, if you merge Nexthink’s extensive data tables with those tools, IT can operate on another level.
For example, our customers are taking advantage of key data fields like Nexthink’s last local IP address and the Digital Experience Score to pin-point the exact location of their remote workers and corroborate this information with key performance data from tools like Power BI, Splunk and ServiceNow.
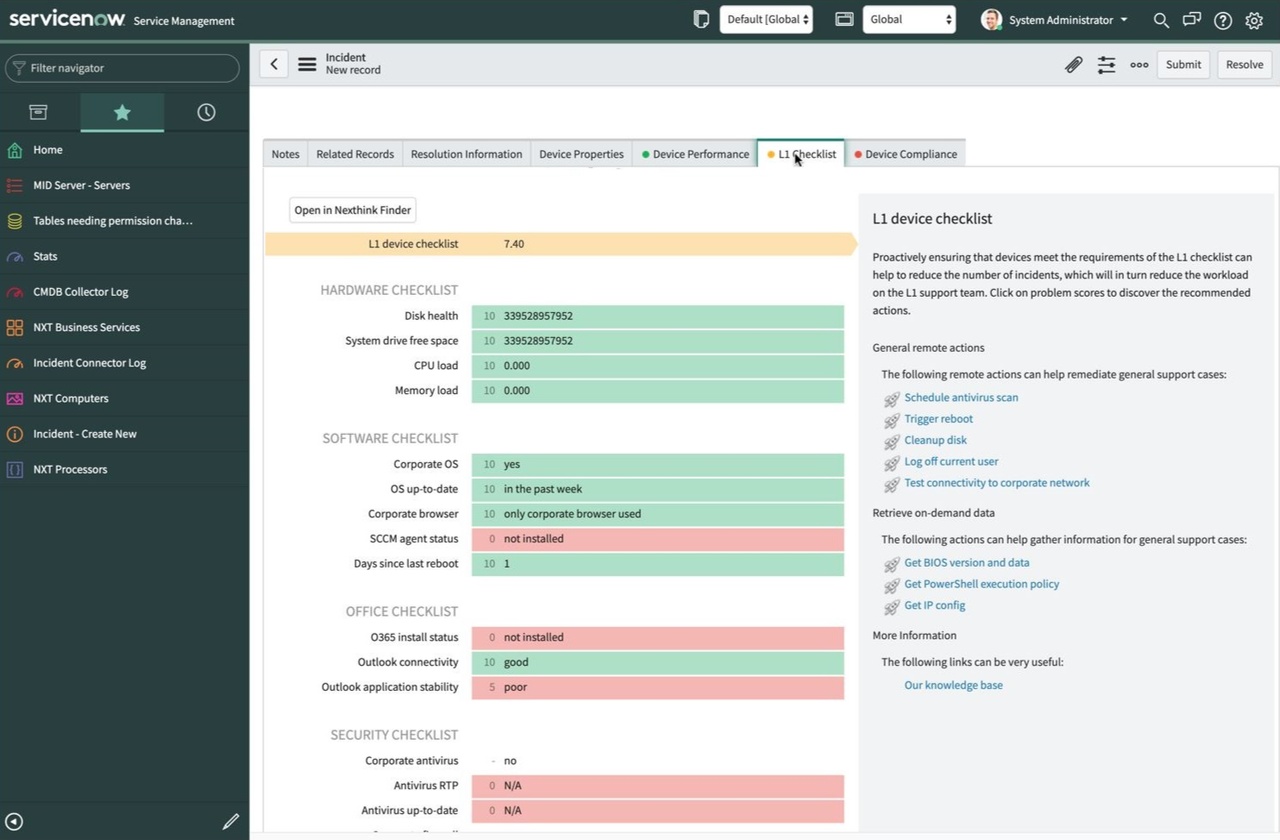
IT can work faster & smarter with our integrations in ServiceNow and other popular ITSM tools
With simple integrations, one-click resolutions and out-of-the-box remote actions, Nexthink makes it easy for IT to act more proactively and fix issues across their entire digital architecture.
7. Safeguarding against Shadow IT
The jump to remote work has thrown millions of employees onto popular collaboration tools like Zoom, Skype, MS Teams, Webex, and others. Call and video quality, certificate expirations, application updates—there are countless tasks that IT has to handle for their remote workers but they have limited resources and time to do it.
Unfortunately, working from home makes it easier for employees to access collaboration tools that sit outside their corporate IT policy. Most IT departments can’t fully monitor and protect their endpoints in a remote environment and this leaves employees vulnerable to cyber attacks and performance degradation.

But thanks to Nexthink’s collector technology, our customers can avoid these situations.
With the collector, IT support has the visibility to determine which software and devices should and shouldn’t be used by employees. For example, one manufacturing customer discovered that 10% of their remote employees were using shadow IT tools to schedule meetings and share important financial documents. Using Nexthink’s messaging features, IT was able to target those exact users and push them onto the correct collaboration tool (MS Teams) in less than an hour.
Ready for anything
This list is just a snapshot of the type of use cases that tech support teams are solving with Nexthink.
For many businesses, remote working is causing significant damage to their bottom line and the well-being of their employees. Nobody knows when things will return back to “normal” but our customers are prepared to support their employees working from anywhere for as long as it takes.
If your IT department needs help solving critical remote technology problems, contact Nexthink today.
Interested in seeing our Remote Working pack in action?
Related posts:
- Remote Working: Encrypt 15k Devices in 3 Days? No problem.
- Your MS Teams Rollout Needs Specific Help—Not General Guidance
- What Your IT Chatbot Can Look Like Running on Full Power
- 8 Websites Every End-User Computing Professional Needs to be Visiting Daily