3-Step Approach to Eliminate the BitLocker Recovery Key Backup Issue using Nexthink
In today’s era of “Work from anywhere”, Data Security & Data Encryption has become a vital security step for organizations world-wide and a key component for security compliance. BitLocker is one of the popular Software Stacks for enforcing encryption on all devices & drives.
Exponential complexity for managing the encryption compliance and the backup of the recovery keys for all devices in the organization has increasingly become a key challenge for EUC Professionals.
The Challenge
Traditionally, corporate devices were domain joined to on-premises Active Directory (AD) and EUC teams leveraged Group Policies to automatically save the BitLocker Recovery Key in AD.
However, as these organizations move from on-premises AD to cloud-based Azure AD or hybrid AD setup, there comes a challenge of managing the backup of BitLocker Recovery Key due to dedicated configurations required to enforce the backup.
Even when all configurations are correct, there is no guarantee that the recovery key gets backed up due to issues like network interruption, local device-related issues etc. This results in BitLocker Recovery Key being available on either, both or none of the ADs.
IT Teams face constraints in resolving the BitLocker Recovery Key backup issue, such as:
- No default mechanism to sync the Recovery Key between AD and Azure AD
- When an enterprise is on a hybrid setup, it is difficult to identify accurately the Active Directory (AD or AAD) to which the Recovery Key might have synced, and which system may be storing the accurate key
- Impossible to identify the impacted machines with discrepancies due to high-security controls in place for Recovery Keys
Let us look at an example of how the EUC Team of a large multinational IT Consulting organization successfully enforced BitLocker Recovery Key Backup on 700 thousand devices using Nexthink.
The Situation
Suddenly, out of the blue, users started seeing this:
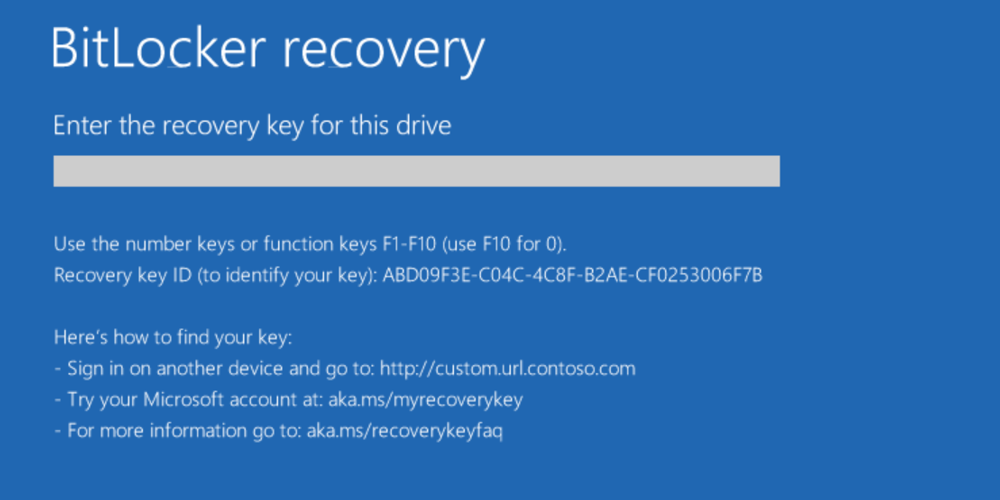
“Ah! Seriously? Again? How can I get rid of this screen”, exclaimed the Sales Director, who was unable to login to his machine due to a prompt that was asking for a recovery key he had no clue about.
Annoyed and frustrated, he reached out to the helpdesk for assistance.
Realizing the prompt to be from BitLocker, the helpdesk analyst went to retrieve the backed-up BitLocker Recovery Key, he was surprised to realize that it wasn’t available either in the Active directory or on Azure AD.
Not seeing any other way to help the Director, IT had to reset the device and restore the data from OneDrive. Luckily, the Director had all data backed up in OneDrive and hence did not face any major data loss. However, the Director lost 3 days while the IT team was working to get his device up and running again and this led to a major escalation within the EUC Team and IT Organization as a whole.
Now, imagine BitLocker Recovery Key not being backed up for hundreds, if not for thousands of employees and them facing the same issue. Think of the time each employee would lose – more importantly, the amount of data loss it could lead to; That would be CATASTROPHIC.
Understanding that this issue could snowball into a major problem especially since the organization was in the process of migrating from on-premises AD to Azure AD, a team was setup at the behest of the EUC Director to design a solution so that no other employee would have their devices restored because of the BitLocker Recovery Key not being backed up.
A 3-Step Approach to Eliminate the BitLocker Recovery Key Backup Compliance Issue
Step 1 – Understanding the Challenge
Immediately after the constitution, the team went about analyzing the root cause for the compliance issue and upon thorough investigation, were able to summarize the challenges under two points
- Discrepancy in the BitLocker Recovery Key between the on-premises AD and Azure AD
- Sync issues between systems – Workstation, AD & Azure AD, causing BitLocker Recovery Key to not backup
Both issues stemmed from various IT issues like
- Multiple Domains
- A combination of domain joined, and non-domain joined devices
- Complex IT management setup comprising of multiple configuration toolset
- Complex and time-consuming migration activities
- Hybrid work setup
Step 2 – Designing a Solution
Now that the team had identified the cause, the solution was simple, they had to force a sync of the recovery key to back up the keys to the on-premises or Azure AD. Since the organization was on a hybrid setup and yet to completely migrate to Azure AD, the team decided to force the recovery key to back up on the on-premises AD.
The team had to simply push a PowerShell Script to all devices to force the backup of recovery key to on-premises AD. The snippet of the script to back up the recovery key is as below –
$BLV = Get-BitLockerVolume -MountPoint “C:”
Backup-BitLockerKeyProtector -MountPoint “C:” -KeyProtectorId BLV.KeyProtector[1].KeyProtectorId
Refer the documentation from Microsoft for more details
Step 3 – The approach to Eliminate BitLocker Recovery Key Backup compliance
Even though the team had the solution, deploying the solution across the entire fleet was easier said than done. Having complete cognisance of the complexity of the IT setup of the organization, the team understood that they could not rely on traditional configuration management solutions like SCCM or Intune to deploy the fix due to issues like lack of broad coverage, reporting capabilities, orchestration etc.
Hence, the team decided to leverage the recently deployed experience management platform, Nexthink as it gave the team some advantages like
- Broad coverage: Nexthink was deployed on 99% of the devices within the organization
- Robust automation engine: Ability to securely deploy and execute PowerShell scripts remotely and repeatedly
- Hybrid Work Setup friendly: Ability to deploy and execute automation irrespective of the employee work style
- Intuitive Dashboarding: Ability to track the progress of compliance through Intuitive dashboards
Thus, a Nexthink Automation script was targeted on the entire organization to force the upload of the Recovery key to AD. This action was further tracked by monitoring Event IDs on the workstations.
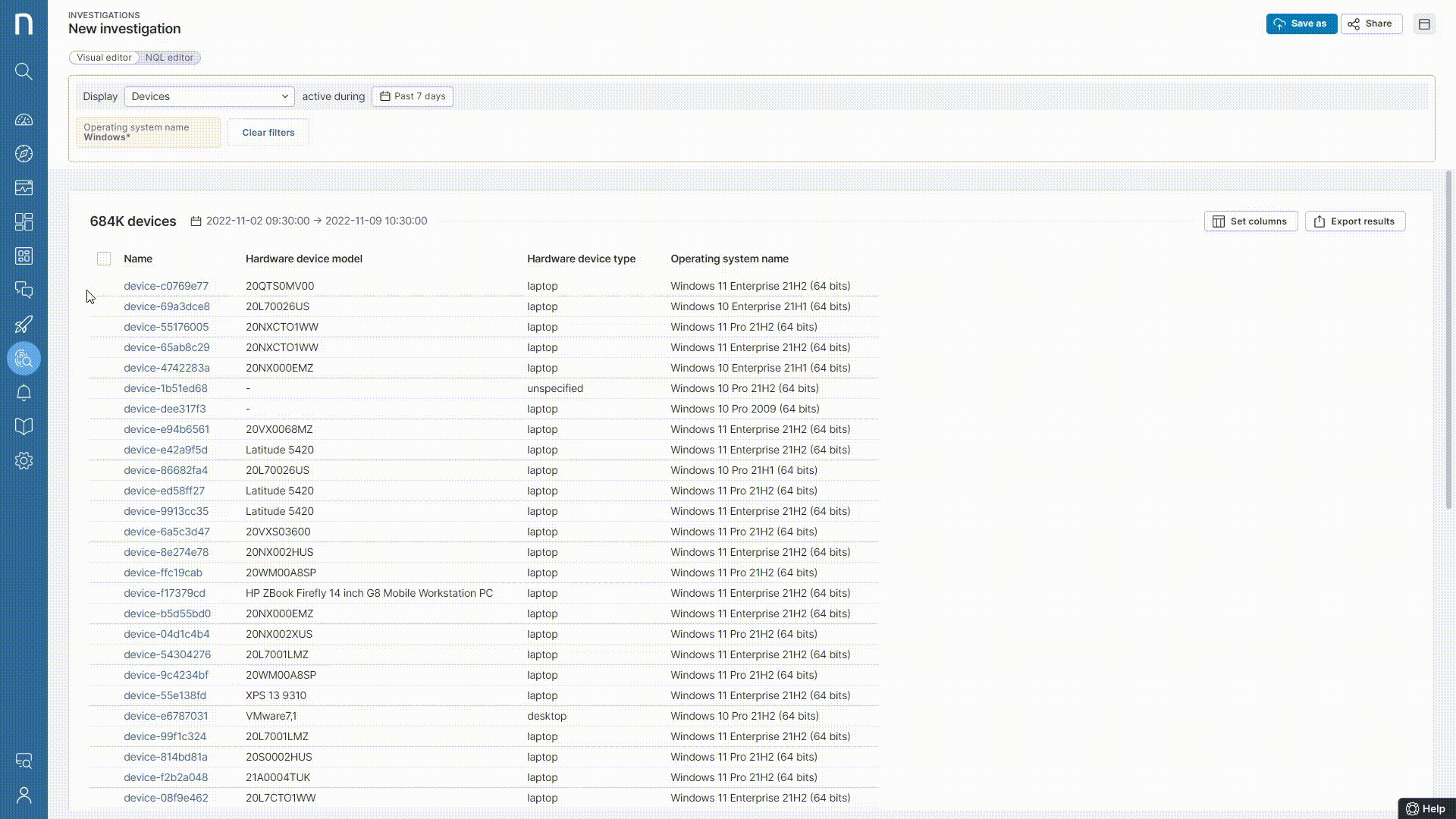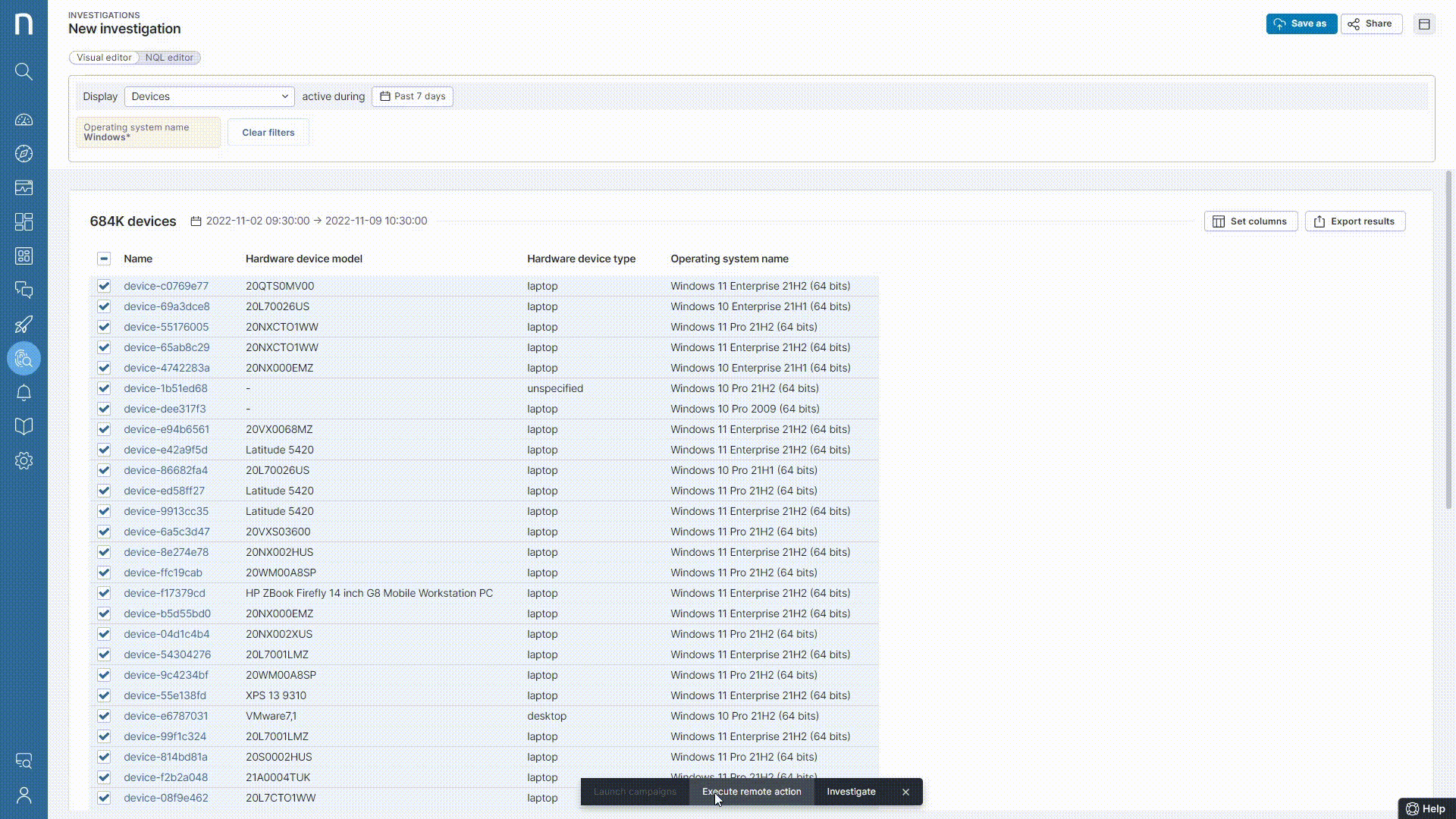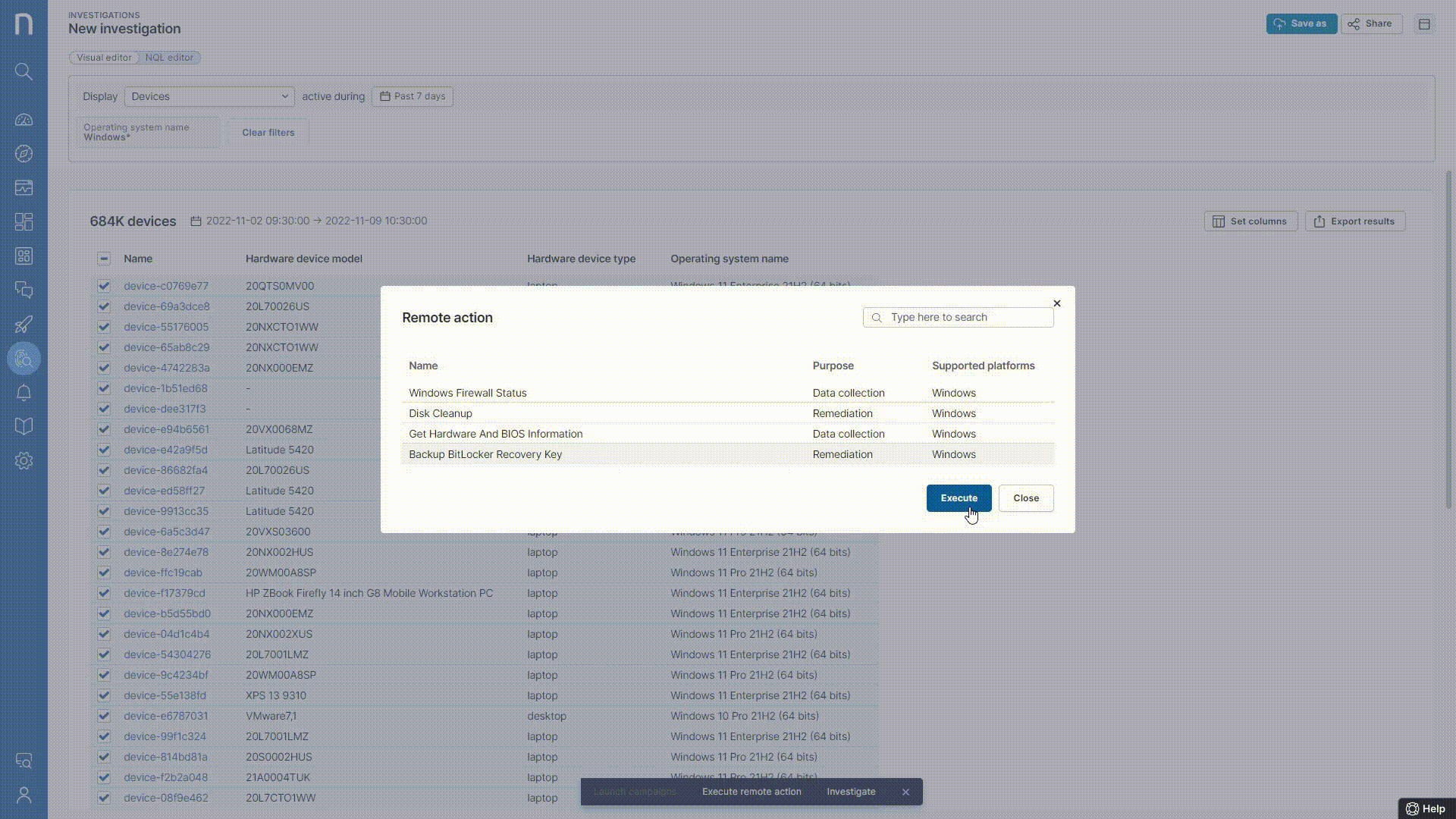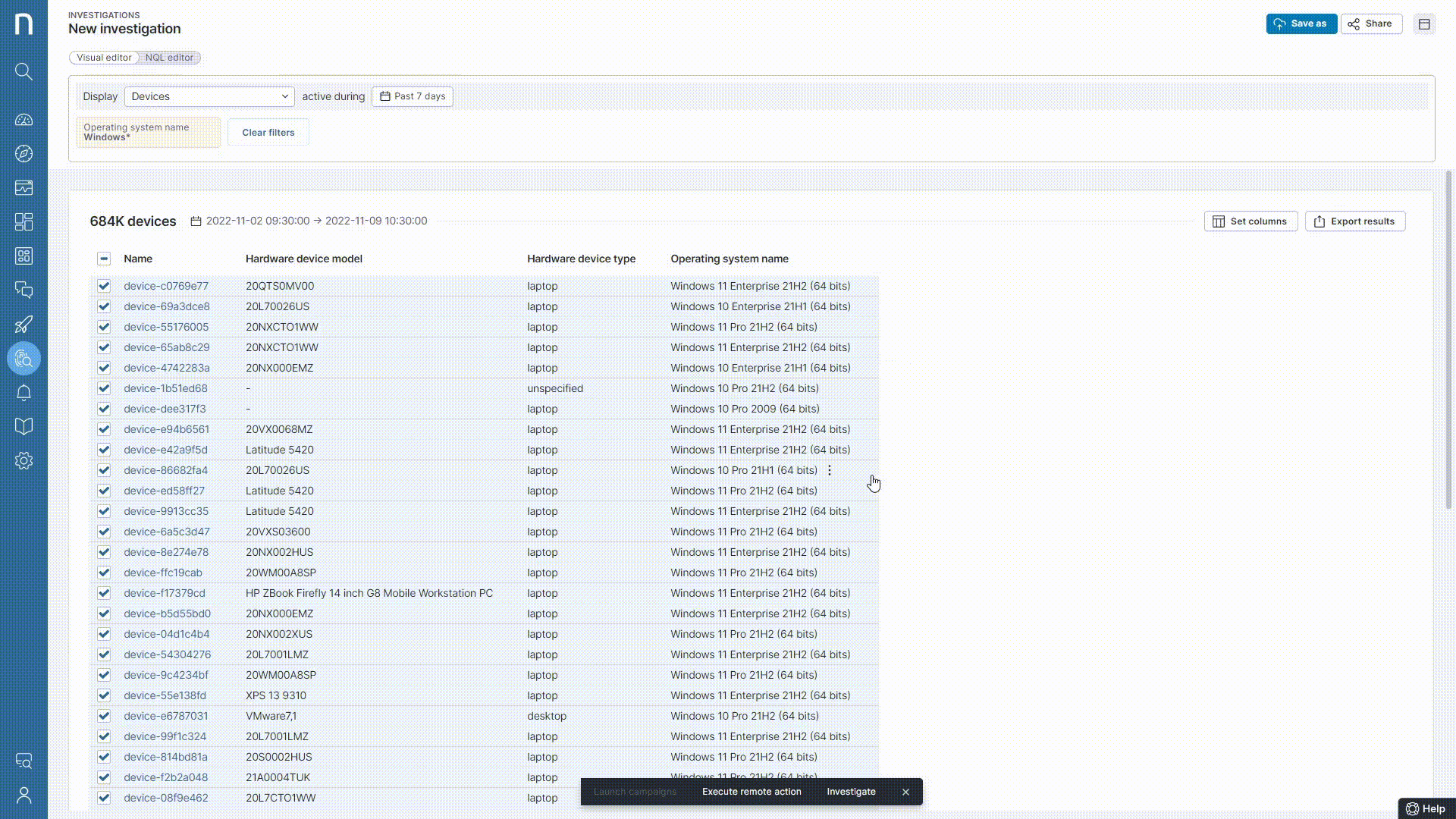
The Below Event IDs confirmed the state & situation on each workstation –
Event 783 – The Recovery Key was already present in AD
Event 784 – The Recovery Key was backed up in AD (Potential problematic device, where the key was not previously present in AD)
Event 785 – The Recovery Key failed to back up (Potential manual effort post the solution)
Outcome
Within a span of a week, the script was successfully deployed across all the devices of the organization and was able to backup recovery key from 85K devices (devices with Recovery Key backed up in Azure AD + devices with Recovery Key not backed up) to AD and verify the existence of the recovery key in AD for 550K devices.
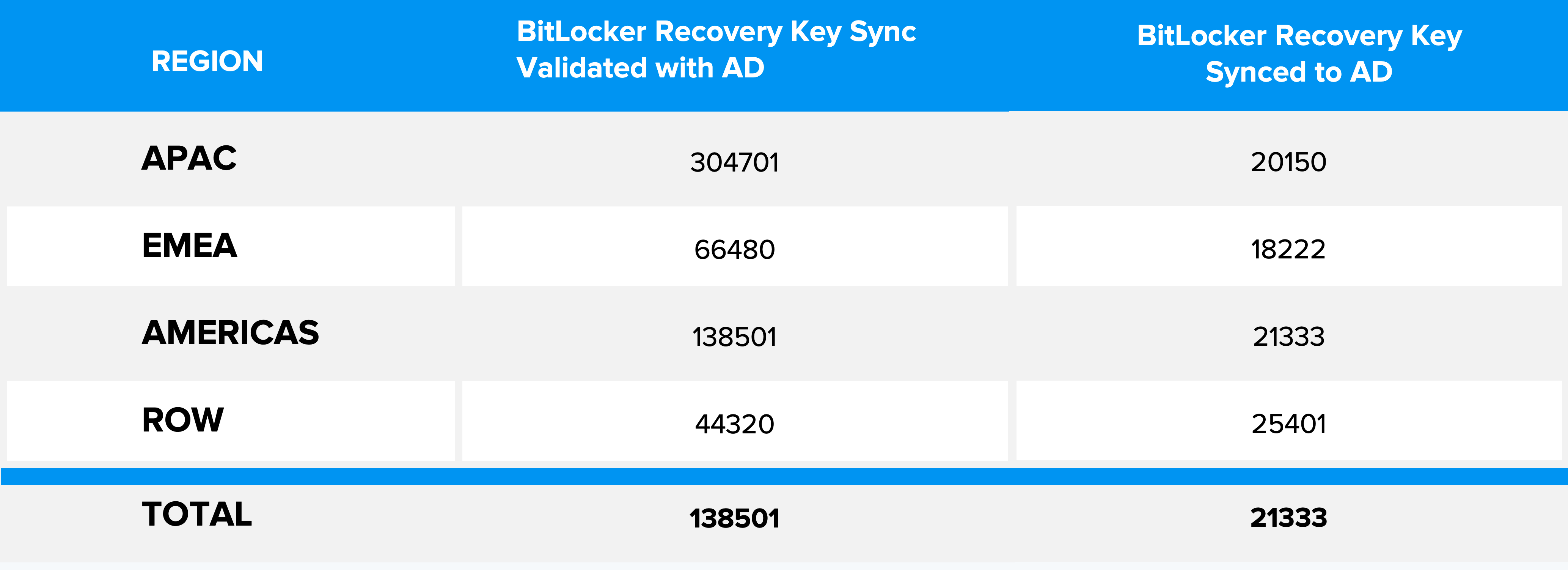
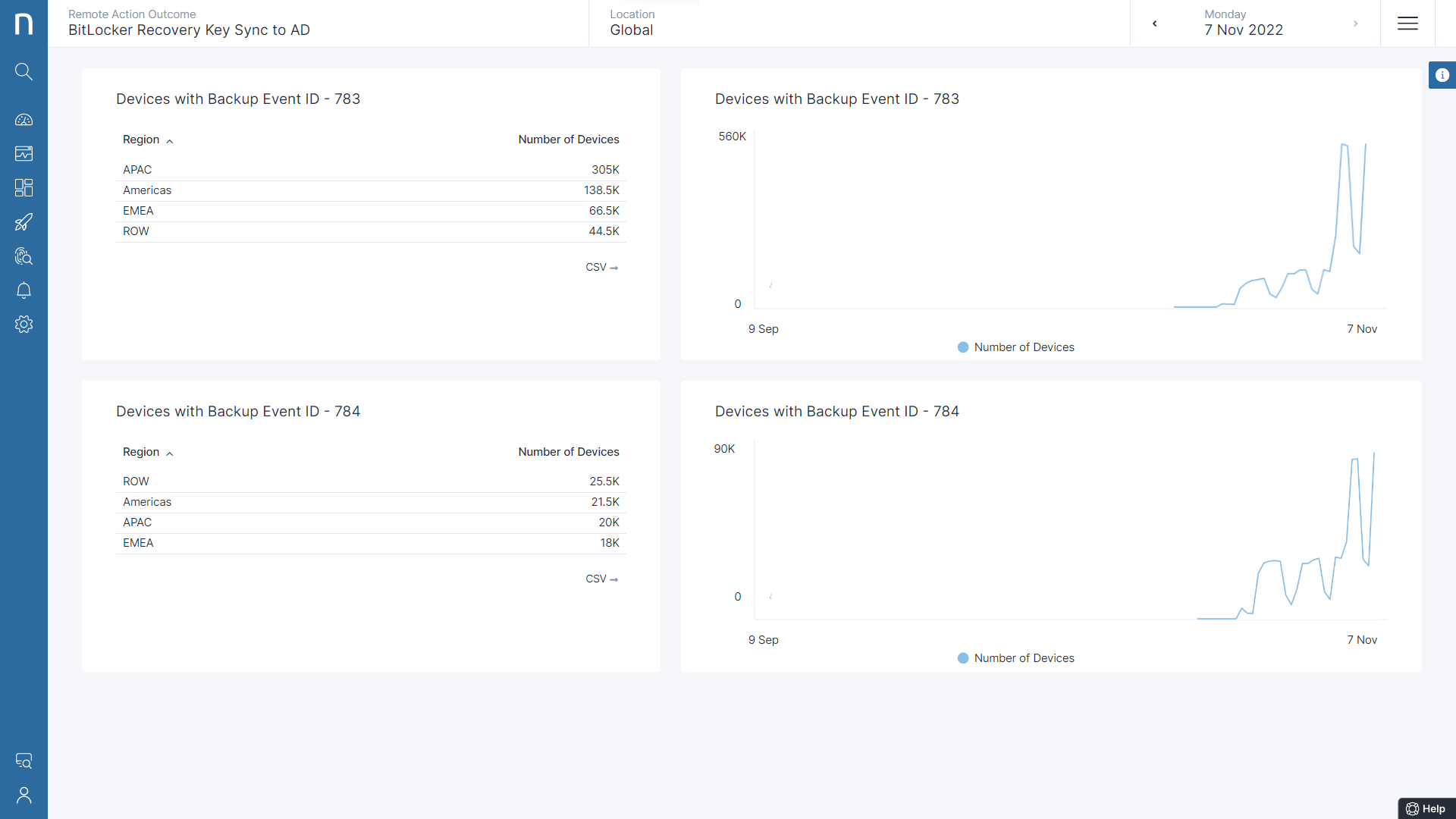
Nexthink Remote Action Tracking Dashboard
Do you need help ensuring compliance?
We are the industry leaders in Digital Employee Experience Management.
Book a demo and we’ll prove it.
Related posts:
- Your MS Teams Rollout Needs Specific Help—Not General Guidance
- What Your IT Chatbot Can Look Like Running on Full Power
- 8 Websites Every End-User Computing Professional Needs to be Visiting Daily
- The Success of Hybrid Work Hinges on Technology